Understanding Elliptic Curve Digital Signature Algorithm (ECDSA)
Sarah MitchellShare
Elliptic Curve Digital Signature Algorithm (ECDSA) represents one of the most sophisticated cryptographic technologies powering modern SSL Certificate security. As digital communications continue to expand across every industry, understanding ECDSA becomes crucial for organizations implementing robust security measures.
Explore everything you need to know about ECDSA and how Trustico® SSL Certificates leverage this advanced technology to deliver superior protection for your digital infrastructure.
At Trustico® we recognize that ECDSA technology forms the backbone of next-generation SSL Certificate security. Our portfolio of both Trustico® branded and Sectigo® branded SSL Certificates incorporates ECDSA algorithms to provide enhanced security with improved performance characteristics. This makes our SSL Certificate solutions ideal for organizations seeking cutting-edge cryptographic protection without compromising operational efficiency.
What is ECDSA Encryption Technology
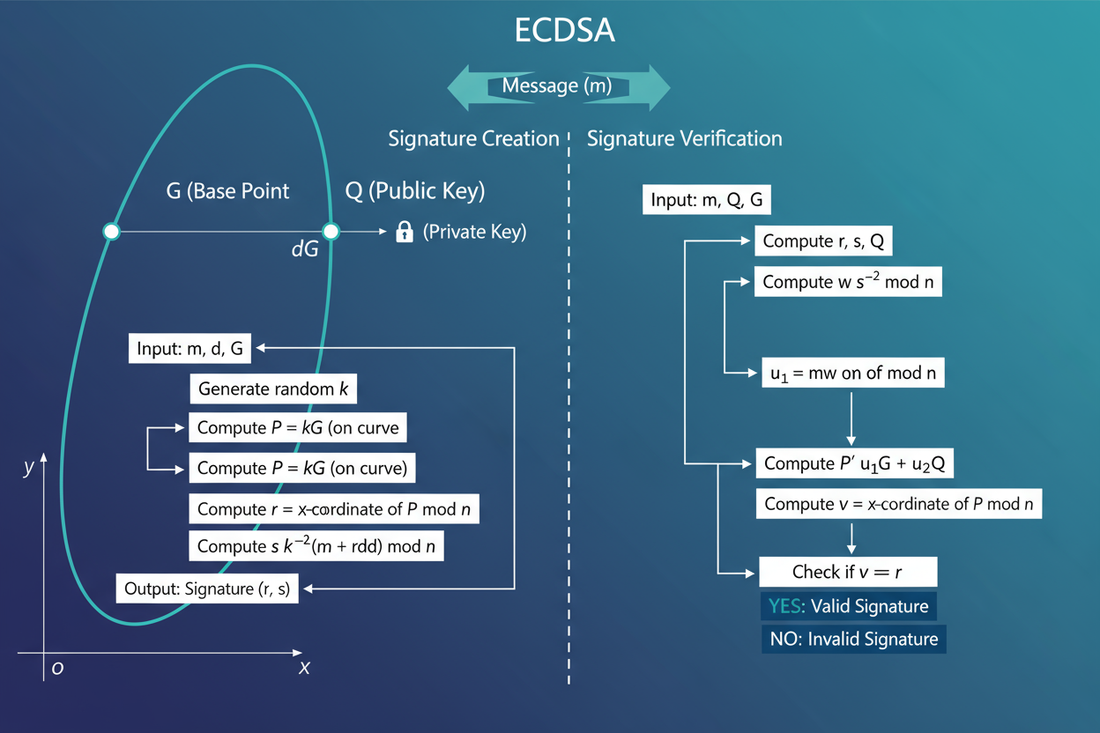
Elliptic Curve Digital Signature Algorithm (ECDSA) represents a sophisticated public key cryptography method built upon the mathematical foundation of elliptic curves over finite fields.
This advanced cryptographic approach utilizes the complex algebraic properties of elliptic curves to create highly secure digital signatures and encryption mechanisms. ECDSA technology has become increasingly important in SSL Certificate implementations due to its ability to provide robust security with significantly smaller key sizes compared to traditional cryptographic methods.
The fundamental strength of ECDSA lies in its mathematical complexity, which makes it computationally infeasible for attackers to break the encryption through brute force methods.
Unlike traditional cryptographic algorithms that rely on the difficulty of factoring large prime numbers, ECDSA derives its security from the elliptic curve discrete logarithm problem. This mathematical foundation allows ECDSA to achieve equivalent security levels using much smaller key sizes, resulting in faster computations and reduced resource requirements.
Trustico® SSL Certificates incorporating ECDSA technology provide organizations with state-of-the-art cryptographic protection. Our SSL Certificate solutions leverage these advanced algorithms to ensure that sensitive data transmissions remain secure while maintaining optimal performance levels.
This combination of security and efficiency makes Trustico® SSL Certificates particularly valuable for high-traffic websites and resource-constrained environments.
ECDSA SSL Certificates : Advanced Security Solutions
ECDSA SSL Certificates represent a revolutionary approach to digital Certificate technology, utilizing elliptic curve cryptography to create digital signatures and establish secure communications channels. These advanced SSL Certificates offer significant advantages over traditional RSA-based SSL Certificates, particularly in terms of computational efficiency and resource utilization.
When organizations choose Trustico® SSL Certificates with ECDSA support, they gain access to cutting-edge cryptographic technology that delivers superior performance without compromising security standards.
The primary advantage of ECDSA SSL Certificates lies in their ability to provide equivalent security levels using dramatically smaller key sizes. For example, a 256-bit ECDSA key provides security comparable to a 3072-bit RSA key, resulting in significantly faster cryptographic operations. This efficiency translates directly into improved website performance, reduced server load, and enhanced user experience across all connected devices and platforms.
Trustico® offers comprehensive ECDSA SSL Certificate solutions through both our Trustico® branded SSL Certificates and our Sectigo® branded SSL Certificate portfolio. These SSL Certificates are designed to meet the diverse security requirements of modern organizations, from small businesses to large enterprises. Our ECDSA-enabled SSL Certificates provide the perfect balance of security, performance, and compatibility, ensuring seamless integration with existing infrastructure while delivering next-generation protection.
Enhanced Security Through Optimized Key Management
One of the most compelling aspects of ECDSA technology is its ability to deliver enhanced security through optimized key management practices. Traditional cryptographic methods require increasingly large key sizes to maintain security against evolving computational threats.
ECDSA addresses this challenge by utilizing the mathematical properties of elliptic curves to achieve superior security with significantly smaller keys, making key management more efficient and practical for organizations of all sizes.
The security advantages of ECDSA extend beyond simple key size reduction. The elliptic curve discrete logarithm problem that underlies ECDSA provides inherent resistance against many attack vectors that threaten traditional cryptographic systems. This mathematical foundation ensures that ECDSA SSL Certificates remain secure against both current and anticipated future threats, providing organizations with long-term cryptographic protection.
Trustico® SSL Certificates leverage these security advantages to provide organizations with robust protection for their digital communications. Our SSL Certificate solutions incorporate industry-leading ECDSA implementations that have been thoroughly tested and validated for security and reliability. This commitment to cryptographic excellence ensures that organizations choosing Trustico® SSL Certificates receive the highest levels of protection available in the market today.
Superior Performance and Computational Efficiency
ECDSA technology delivers exceptional performance benefits that make it particularly valuable for high-demand applications and resource-constrained environments. The smaller key sizes inherent in ECDSA algorithms result in faster signature generation and verification processes, reduced memory requirements, and lower computational overhead. These performance improvements translate directly into tangible benefits for organizations implementing SSL Certificates in their infrastructure.
The computational efficiency of ECDSA becomes particularly apparent in environments where cryptographic operations must be performed frequently or where processing resources are limited. Mobile applications, IoT devices, and high-traffic web servers all benefit significantly from the reduced computational requirements of ECDSA-based SSL Certificates. This efficiency enables organizations to maintain strong security while optimizing system performance and resource utilization.
Trustico® SSL Certificates incorporating ECDSA technology provide organizations with these performance advantages while maintaining the highest security standards. Our SSL Certificate solutions are optimized to deliver maximum efficiency without compromising cryptographic strength, ensuring that organizations can achieve their performance objectives while maintaining robust security posture. This optimization makes Trustico® SSL Certificates ideal for organizations seeking to balance security requirements with operational efficiency.
Energy Efficiency and Environmental Considerations
The reduced computational requirements of ECDSA technology translate directly into improved energy efficiency, making it an environmentally conscious choice for organizations committed to sustainable operations.
The smaller key sizes and faster processing times associated with ECDSA algorithms result in lower power consumption across all system components, from individual devices to large-scale data centers. This energy efficiency provides both environmental and economic benefits for organizations implementing ECDSA-based SSL Certificates.
Energy efficiency becomes particularly important in battery-powered devices and mobile applications where power consumption directly impacts device usability and operational costs. ECDSA SSL Certificates enable these devices to maintain strong security while extending battery life and reducing overall power requirements. This efficiency makes ECDSA technology essential for IoT deployments and mobile applications where energy conservation is critical.
Trustico® recognizes the importance of environmental sustainability in modern business operations. Our SSL Certificate solutions incorporating ECDSA technology help organizations reduce their environmental footprint while maintaining superior security standards. This commitment to both security and sustainability makes Trustico® SSL Certificates an excellent choice for organizations seeking to balance their security requirements with their environmental responsibilities.
Comprehensive Application Portfolio
ECDSA SSL Certificates support a wide range of applications across diverse industries and use cases. Secure web browsing through HTTPS connections represents the most common application, where ECDSA technology protects data transmissions between web browsers and servers. This protection ensures that sensitive information remains confidential and tamper-proof during transmission, providing users with confidence in the security of their online interactions.
Code signing applications represent another critical use case for ECDSA SSL Certificates. Software developers utilize these SSL Certificates to digitally sign applications and updates, providing users with verification that the software originates from a trusted source and has not been modified during distribution. This application of ECDSA technology helps prevent malware distribution and ensures software integrity across the entire software supply chain.
Document authentication and e-mail security applications also benefit significantly from ECDSA technology. Digital document signing using ECDSA SSL Certificates provides non-repudiation and integrity verification for critical business documents. E-Mail security implementations utilize ECDSA for both signing and encryption operations, ensuring that e-mail communications remain private and authentic. Trustico® SSL Certificates support all these applications through our comprehensive SSL Certificate portfolio.
ECDHE_ECDSA Protocol Implementation
The ECDHE_ECDSA protocol combines Elliptic Curve Diffie-Hellman Ephemeral key exchange with Elliptic Curve Digital Signature Algorithm authentication to provide comprehensive security for communication channels.
This protocol implementation represents the state-of-the-art in secure communications, offering both perfect forward secrecy and strong authentication capabilities. Understanding ECDHE_ECDSA is crucial for organizations implementing advanced SSL Certificate solutions.
The ECDHE component provides ephemeral key exchange capabilities, generating unique session keys for each communication session. This approach ensures that even if long-term private keys are compromised, individual session communications remain secure. The ephemeral nature of these keys provides perfect forward secrecy, significantly enhancing the overall security posture of SSL Certificate implementations.
The ECDSA component handles authentication and digital signature operations, ensuring that communicating parties can verify each other identity and detect any tampering with transmitted data.
This dual-layer approach provides comprehensive protection against both eavesdropping and man-in-the-middle attacks. Trustico® SSL Certificates support ECDHE_ECDSA implementations, providing organizations with access to these advanced security capabilities.
Security Considerations and Vulnerability Management
While ECDSA technology provides exceptional security benefits, proper implementation requires careful attention to potential vulnerabilities and security considerations. Random number generation represents one of the most critical aspects of ECDSA security, as weak or predictable random numbers can compromise the entire cryptographic system.
Organizations must ensure that their ECDSA implementations utilize cryptographically secure random number generators to maintain security integrity.
Implementation flaws represent another significant security consideration for ECDSA deployments. Improper curve parameter selection, insufficient input validation, and edge case handling errors can introduce vulnerabilities that attackers might exploit.
Side-channel attacks pose additional risks to ECDSA implementations, particularly in environments where attackers might have physical access to systems or can monitor system behavior. These attacks exploit timing variations, power consumption patterns, or electromagnetic emissions to extract cryptographic keys.
Trustico® SSL Certificates incorporate protections against these attack vectors, ensuring robust security across diverse deployment scenarios.
Key Management Best Practices
Effective key management represents a critical component of successful ECDSA SSL Certificate deployment. Organizations must implement comprehensive key management practices that address key generation, distribution, storage, rotation, and destruction throughout the entire SSL Certificate lifecycle.
Proper key management ensures that the security benefits of ECDSA technology are fully realized while minimizing operational risks and compliance challenges.
Secure key generation requires the use of cryptographically secure random number generators and proper entropy sources. Organizations should ensure that their key generation processes meet industry standards and regulatory requirements for their specific industry and geographic location. Trustico® provides guidance and support for proper key generation practices, helping organizations establish secure foundation for their SSL Certificate deployments.
Key storage and protection mechanisms must be designed to prevent unauthorized access while enabling legitimate cryptographic operations. Hardware security modules, secure key stores, and access control systems all play important roles in comprehensive key management strategies.
Comparative Analysis : ECDSA vs RSA Technology
Understanding the differences between ECDSA and RSA technologies helps organizations make informed decisions about their SSL Certificate requirements.
RSA has provided reliable cryptographic security for decades and remains widely supported across diverse platforms and applications. However, RSA requires increasingly large key sizes to maintain security against evolving computational threats, resulting in higher resource requirements and reduced performance.
ECDSA addresses the limitations of RSA through its innovative use of elliptic curve mathematics. The security of ECDSA derives from the elliptic curve discrete logarithm problem, which provides equivalent security using much smaller key sizes. This mathematical advantage translates into significant performance benefits, making ECDSA particularly valuable for resource-constrained environments and high-performance applications.
The choice between ECDSA and RSA often depends on specific organizational requirements, including performance needs, compatibility constraints, and security objectives.
Trustico® SSL Certificates support both ECDSA and RSA technologies, providing organizations with flexibility to choose the most appropriate cryptographic approach for their specific requirements.
Future-Proofing Your SSL Certificate Strategy
As cryptographic threats continue to evolve, organizations must consider the long-term viability of their SSL Certificate strategies. ECDSA technology provides excellent resistance against current attack methods while maintaining efficiency advantages that will become increasingly important as computational demands continue to grow.
Organizations implementing ECDSA SSL Certificates today position themselves well for future security challenges and technological developments.
Quantum computing represents a potential future threat to current cryptographic methods, including both ECDSA and RSA. However, ECDSA smaller key sizes and computational efficiency make it easier to implement quantum-resistant upgrades when they become available. This adaptability provides organizations with additional future-proofing benefits when choosing ECDSA-based SSL Certificate solutions.
Trustico® remains committed to staying at the forefront of cryptographic technology developments. Our SSL Certificate solutions are designed to evolve with changing security requirements and technological advances.
Organizations choosing Trustico® SSL Certificates benefit from our ongoing investment in research and development, ensuring access to the latest security innovations and protection against emerging threats.
Implementing Trustico® SSL Certificates with ECDSA Technology
Trustico® provides comprehensive SSL Certificate solutions that leverage ECDSA technology to deliver superior security and performance. Our portfolio includes both Trustico® branded and Sectigo® branded SSL Certificates with ECDSA support, providing organizations with flexible options to meet their specific security requirements. Our SSL Certificates are designed for easy integration with existing infrastructure while providing advanced cryptographic protection.
Organizations choosing Trustico® SSL Certificates gain access to industry-leading cryptographic technology, comprehensive technical support, and ongoing security updates. Our commitment to excellence in both technology and service ensures that organizations receive maximum value from their SSL Certificate investments while maintaining the highest levels of security protection available in the market today.



